Which Of The Following Identifies An Operating System Or Network Service
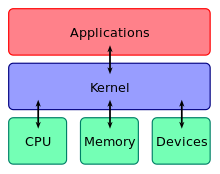
Which of the following identifies an operating system or network service. Operating Systems generally identifiesauthenticates users using following three ways. IBM Microsoft Novell Red Hat and Sun offer certifications that test knowledge of their operating systems. Kernel is the first part of operating system to load into memory during booting.
ActiveX controls can run on any browser platform. In the Windows operating system the NetBIOS service is commonly targeted by attackers because diverse information can be obtained including usernames share names and service information. Statements 1and 2 are correct.
AltF8 is the key combination that closes pop-up windows. Here are three statements that relate to Chapter 4. 5 All of the above.
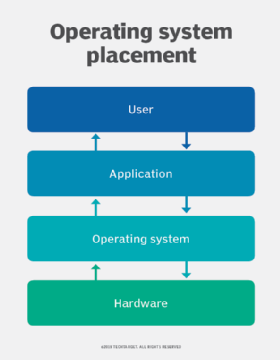
By this the client computer can establish indirect network connection to another network. Kernel is the program that constitutes the central core of the operating system. The most popular implementation of DNS is the Unix Internet Name Domain.
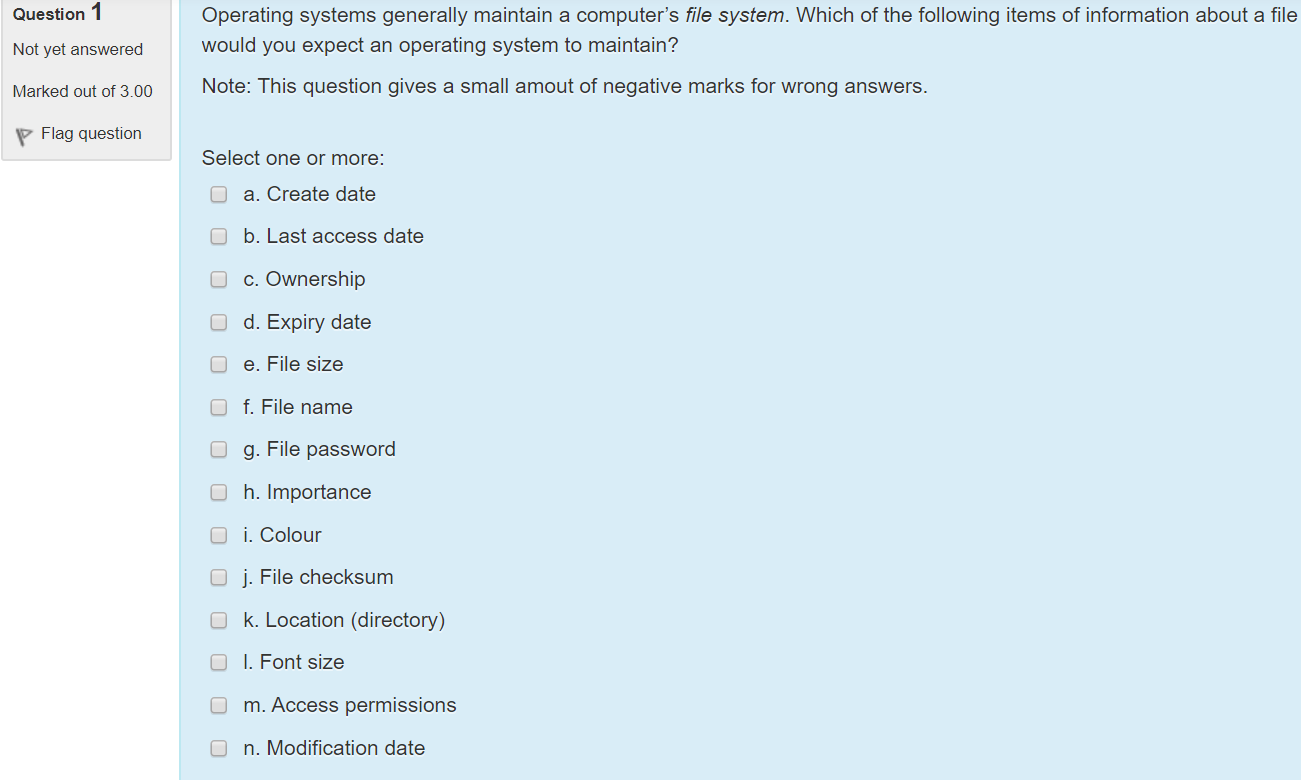
Let us have a look at your work and suggest how to improve it. Which of the following is an Operating System. Input validation is a process that ensures the correct usage of data.
You are configuring the firewall separating the DMZ from the private network so that traffic from DMZ hosts is allowed into the private. Both SSH and Telnet are used to connect to devices over the network and so are both used in-band. 9th - 12th grade.
A with external access. It requires more resources than a typical system such as multiple processors massive amounts of RAM fast and abundant hard drive space and one or more fast network cards.
The most popular implementation of DNS is the Unix Internet Name Domain.
TCPIP uses its own four-layer architecture that includes the Network Interface Internet Transport and Application layers. Computing Systems Test Digital Literacy Quiz - Quizizz. A proxy server is a computer that acts as a gateway between a users computer and the Internet. Google Android is best classified as one of the fastest growing of these. True An attacker can deprive the system owner of the ability. Input validation is a process that ensures the correct usage of data. Statements 1and 2 are correct. With it you have a 9999 percent availability service level agreement from Azure powered by a global network of Microsoft-managed datacenters. The proxy server is also called application level gateway.
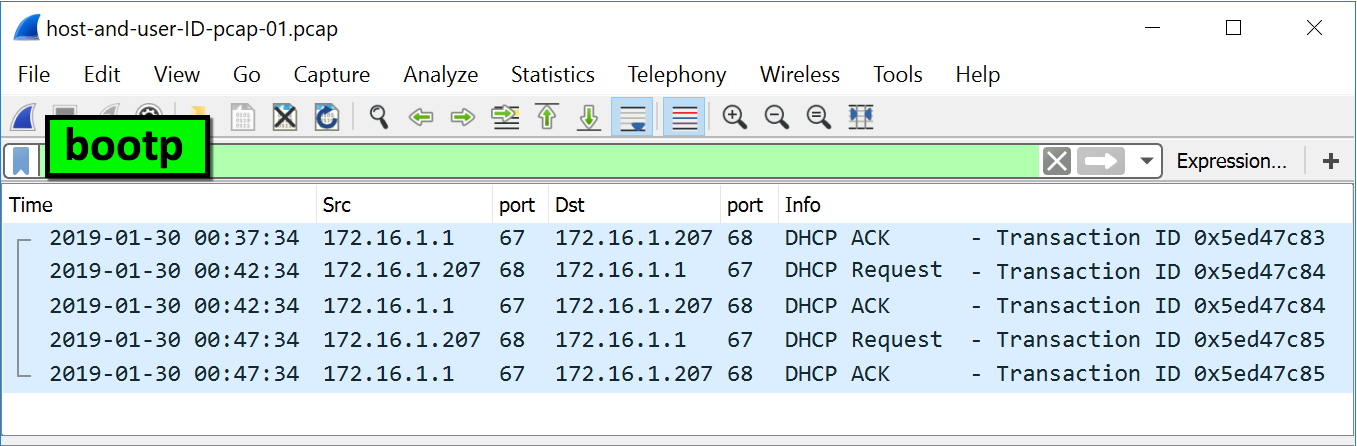
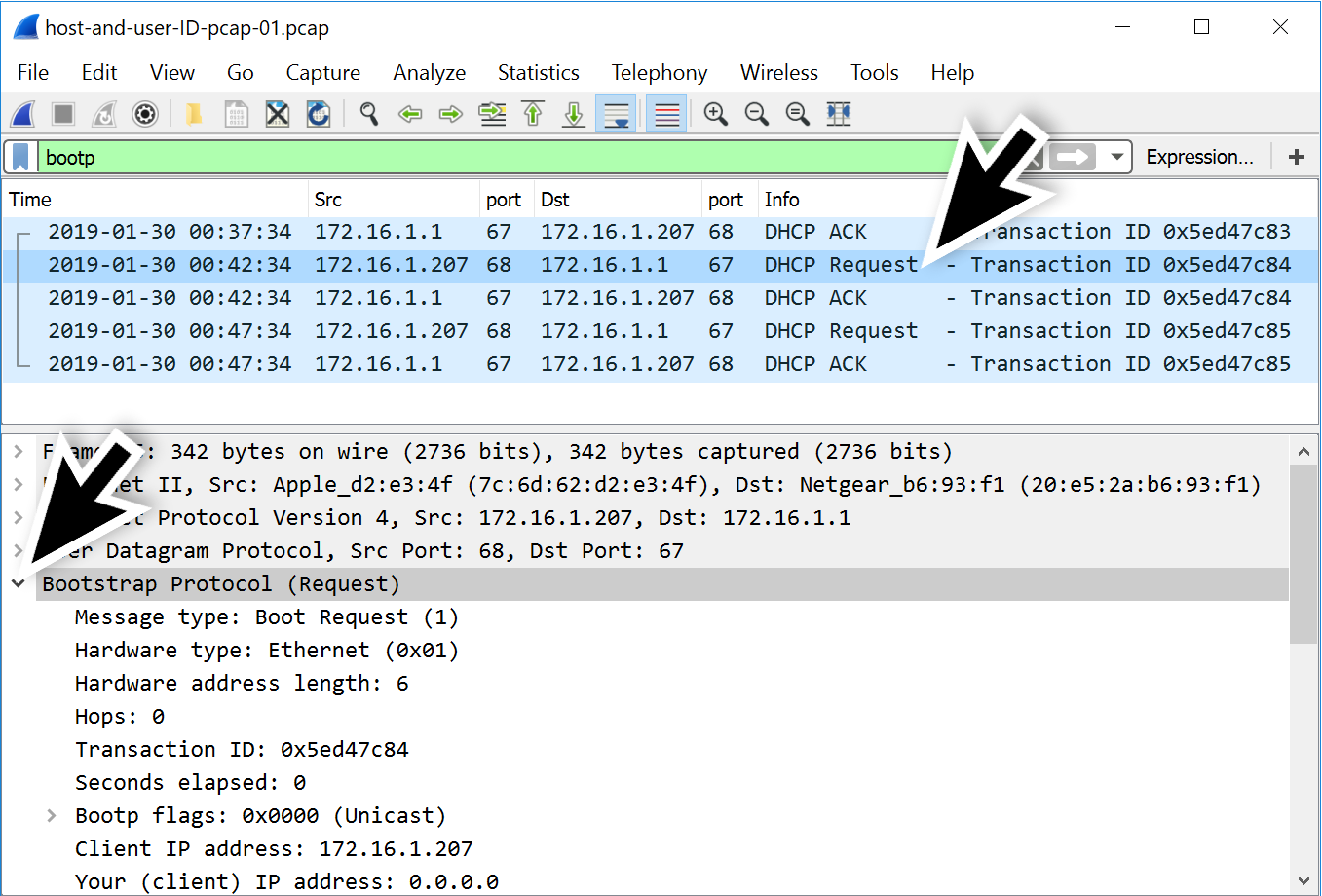
You are configuring the firewall separating the DMZ from the private network so that traffic from DMZ hosts is allowed into the private. Kernel is the program that constitutes the central core of the operating system. You have decided to perform a double blind penetration test. Uses the 199126129024 network address range in its DMZ. Zenmap is a graphical interface for _____ a port scanning tool that can quickly identify hosts and detect what operating system and services are running on them and all without privileged access. Operating Systems generally identifiesauthenticates users using following three ways. Kernel is the first part of operating system to load into memory during booting.





















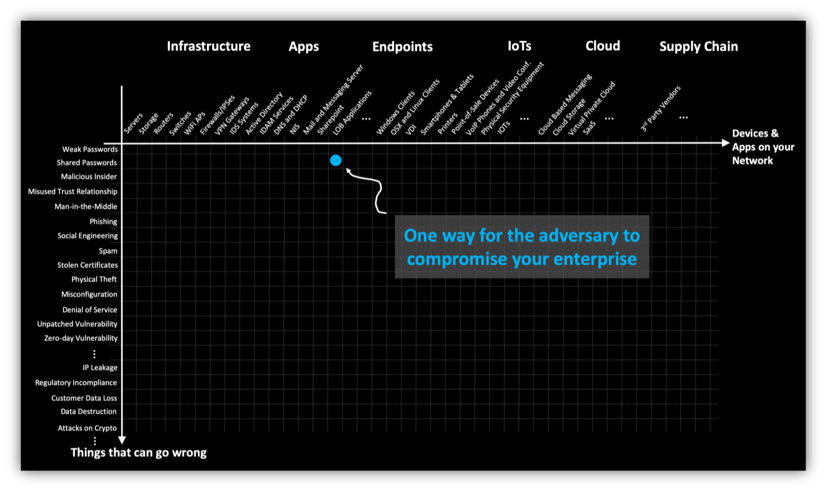
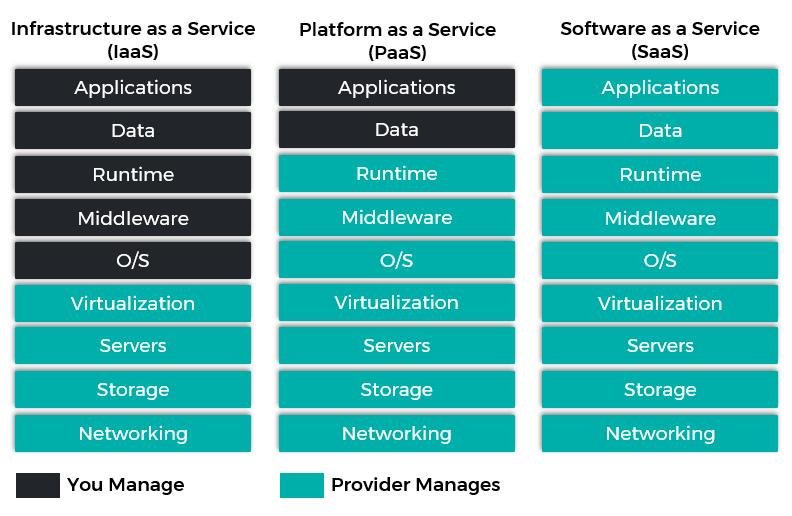

Post a Comment for "Which Of The Following Identifies An Operating System Or Network Service"